Protect Your Data with Advanced, Reliable Security
Bold BI prioritizes your data security, ensuring complete protection through seamless integration with your existing infrastructure. Whether on-premises or cloud-hosted, trust Bold BI to deliver robust, flexible, and compliant data security.
No credit card required.
Trusted by world-class companies







Advanced Security Features for Maximum Data Protection
Ensure robust security with complete data control, encryption, and trusted authentication. Protect your dashboards, data, and user access with enterprise-grade security measures.
Complete Data Control
Maintain absolute ownership of your data. Bold BI ensures full control whether hosted on a private data center or a public cloud—without Syncfusion accessing or storing it. IP whitelisting allows only trusted addresses, enhancing perimeter security.
Granular Row-Level Security
Control data access precisely by filtering dashboard data at the row level. Users and groups only view data authorized for them, enabling secure and efficient multi-user or multi-tenant scenarios with a single dashboard.
Streamlined Single Sign-On (SSO)
Integrate seamlessly with existing authentication systems using SSO. Simplify logins, enhance security, and streamline access. Configure CORS policies to allow only authorized domains, securing authentication further.
Encryption at Rest
Bold BI encrypts sensitive data using unique private keys generated during installation. On-premises deployments benefit from AES-256 encryption for metadata like credentials and access tokens, with support for key rotation.
Secure SSL Encryption for Data Transfer
Bold BI ensures end-to-end encrypted data transmission with SSL security, safeguarding interactions between clients, servers, and databases. Prevent interception and maintain the integrity and confidentiality of your business data transfers.
Trusted Authentication
Validate every access request with trusted authentication. Use providers like Azure AD, Okta, or Auth0, JWT, or Bold BI’s built-in authentication. External authorization servers can issue short-lived JWT tokens for secure embedded access.
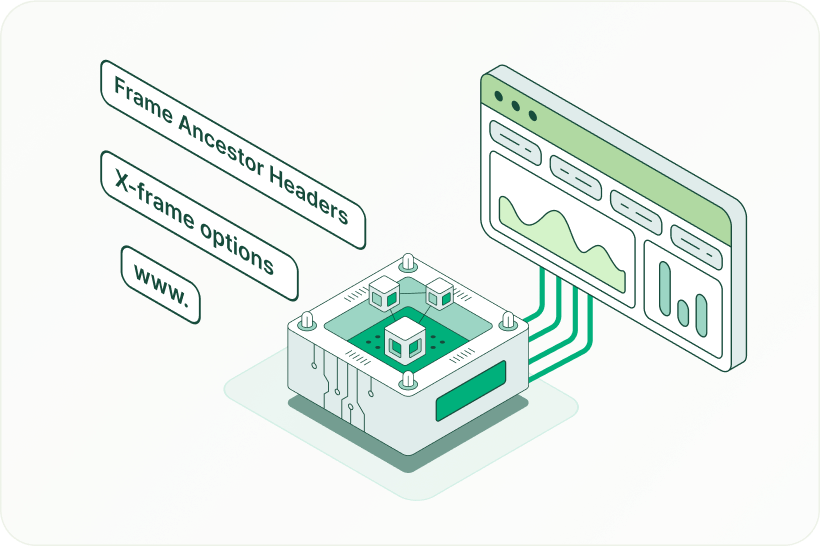
Advanced embedded security
Strengthen embedded security with domain restrictions, X-Frame-Options, and frame-ancestor headers to prevent clickjacking. Apply Content Security Policy (CSP) headers to control the loading of browser-based resources.
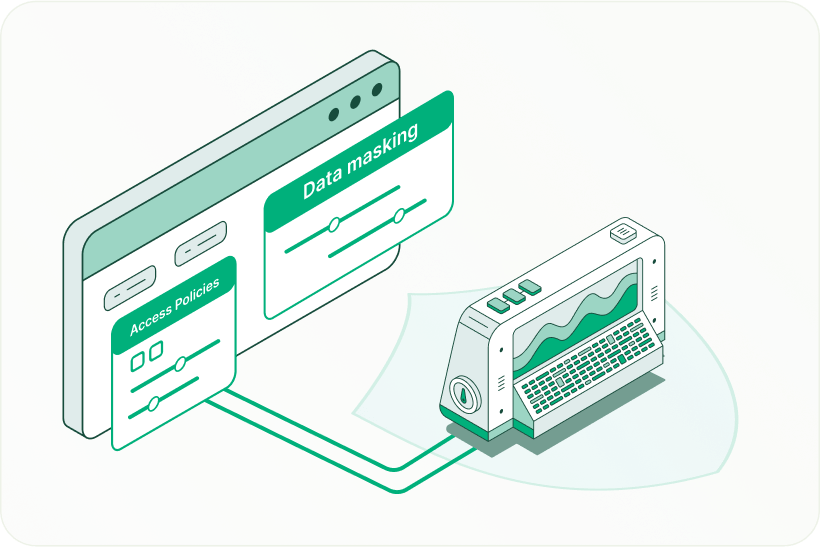
Centralized Security Management
Control all critical security settings from a centralized Security Configuration Panel in the Bold BI Admin UI. Configure access policies, data masking (if available), authentication protocols, encryption options, and more—all from one place for streamlined governance.
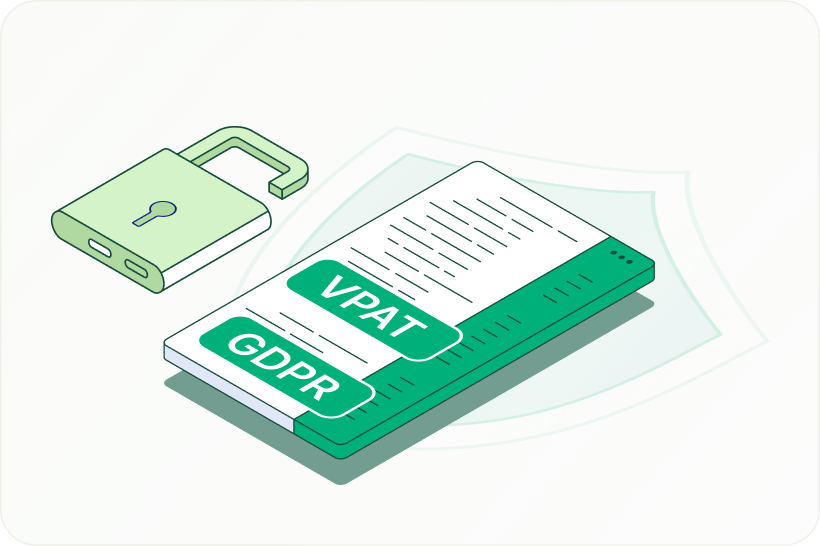
Customer Compliance
Bold BI is committed to upholding the highest standards of data protection and privacy. We adhere to globally recognized compliance frameworks and undergo independent audits to validate our security and privacy practices. Bold BI is compliant with GDPR, SOC 2 Type 2, VPAT (Section 508 accessibility standards), and APAC regional regulations, ensuring that customer data is handled securely and responsibly across regions.
Secure Your Business Insights
with Bold BI
Protect sensitive data with enterprise-grade security features while delivering powerful analytics.
No credit card required.

